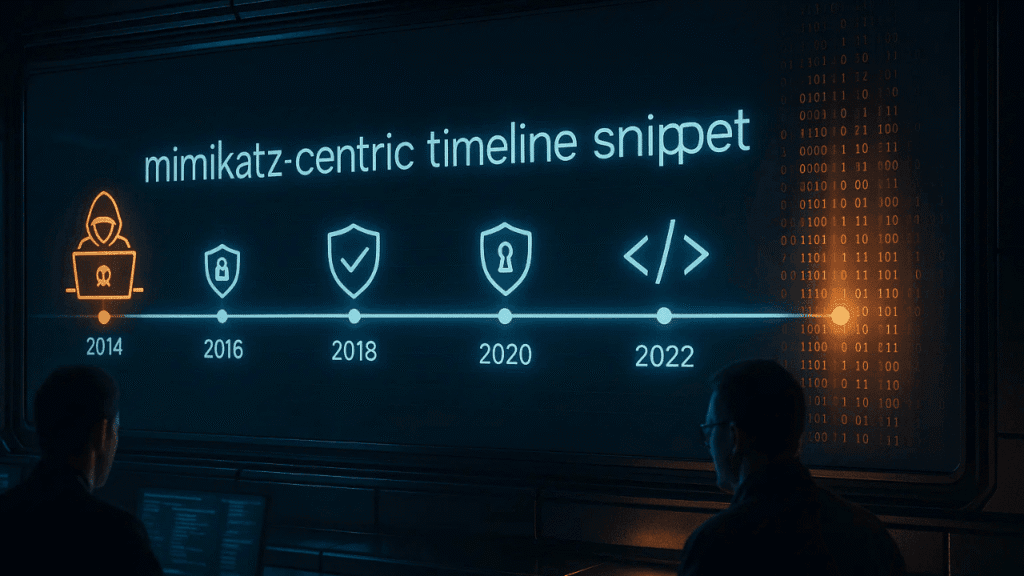
A mimikatz-centric timeline snippet gives readers a compact, focused chronology of events, techniques, and responses tied to one of the most influential credential tools in Windows security history. Security practitioners, incident responders, and curious readers benefit from a clear, chronological view that links releases, attack campaigns, defensive changes, and practical detection tips. This article provides a detailed, human-friendly walkthrough so you can understand when and how mimikatz shows up in an intrusion and what defenders can do about it.
Origins and early development of mimikatz
The story of mimikatz begins with deep exploration of Windows authentication internals. Early experiments led to the creation of a tool capable of reading authentication artifacts from memory and system stores. A mimikatz-centric timeline snippet should start here because the tool’s genesis explains its capabilities: memory scraping, ticket extraction, and credential manipulation. Understanding the original motivations clarifies why the tool became both a red team staple and a favorite of attackers.
Key technical milestones to include in a mimikatz-centric timeline snippet
A meaningful mimikatz-centric timeline snippet should highlight pivotal technical changes. Include milestones such as the addition of Kerberos ticket operations, support for pass-the-hash techniques, golden and silver ticket creation, and modules that target specific Windows subsystems. Each milestone represents a broadened attacker capability or a new red team capability used for testing defenses.
Points to include:
- Memory extraction from the Local Security Authority Subsystem Service (LSASS).
- Kerberos ticket manipulation and ticket forging.
- Pass-the-hash and credential harvesting features.
- Added modules for modern Windows authentication components.
These items will help readers quickly see how mimikatz evolved from a proof-of-concept into a multi-module toolkit.
Real-world incidents that belong in a mimikatz-centric timeline snippet
To make a mimikatz-centric timeline snippet actionable, add concrete incidents where credential dumping changed the course of an intrusion. Many notable campaigns used credential theft to move laterally and escalate privileges. When you build your timeline snippet, show the sequence: initial access, credential dumping with mimikatz, lateral movement, and persistence. That sequence helps incident responders reconstruct intrusions and prioritize containment.
Suggested incident-focused timeline entries:
- Initial disclosure or public release of the tool and immediate adoption by penetration testers.
- Early misuse in high-profile breaches that relied on credential extraction.
- Inclusion of credential dumping in destructive and ransomware campaigns.
- Ongoing dual use by defenders and attackers alike.
How defenders changed their posture and should be represented in the mimikatz-centric timeline snippet
Defensive evolution is a major theme in any mimikatz-centric timeline snippet. As credential dumping tactics spread, vendors and platform owners introduced mitigations: disabling legacy authentication storage, LSA protection options, improved auditing, and host-based detection of suspicious memory reads. Each defensive change is a turning point in your timeline snippet because it shows the arms race between attackers and defenders.
Defensive elements to map:
- Configuration changes that reduce credential exposure.
- Detection primitives (LSASS read attempts, suspicious token usage).
- Endpoint detection and response enhancements.
- Best practice adoption such as credential hygiene and least privilege.
Practical guidance: what logs and artifacts to collect for your mimikatz-centric timeline snippet
When an analyst assembles a mimikatz-centric timeline snippet from forensic data, they need specific artifacts. Collect these items to build a reliable snippet of activity:
- LSASS process access logs or EDR alerts indicating memory reads.
- Event logs showing authentication anomalies and lateral logons.
- Kerberos ticket inventories and unexpected ticket creation.
- Process creation logs for suspicious tools or commands.
- Network logs showing lateral SMB/RDP activity following credential extraction.
Collecting and correlating these artifacts lets you turn raw events into a compact mimikatz-centric timeline snippet that tells the story of the intrusion.
Detection strategies to include in the mimikatz-centric timeline snippet
Detection is central to any useful mimikatz-centric timeline snippet. Practical detection strategies include monitoring for processes reading LSASS memory, unusual use of credential APIs, and sudden proliferation of service tickets. Layered detection—combining telemetry from endpoint agents, Windows logs, and network sensors—produces the richest timeline snippet.
Detection tactics:
- Monitor for untrusted processes opening LSASS with read access.
- Alert on suspicious lsass.exe memory dump attempts or tools calling credential APIs.
- Flag anomalies in Kerberos ticket issuance patterns.
- Use behavioral baselines to detect sudden lateral movement after credential theft.
Reconstructing an incident: example mimikatz-centric timeline snippet
Here is a concise example of the type of chronology you could present as a mimikatz-centric timeline snippet during incident response:
- Initial compromise via phishing link leads to command execution on host A.
- Attacker executes reconnaissance commands and harvests local credentials.
- A process is observed opening LSASS memory; EDR flags unusual read behavior.
- Mimikatz command run to extract NTLM hashes and Kerberos tickets.
- Attacker uses extracted credentials to authenticate to host B via SMB.
- Golden ticket forged and used to access domain controller resources.
- Persistence mechanism established; lateral movement continues.
An analyst can expand each line with timestamps, hostnames, and forensic artifacts to form a full mimikatz-centric timeline snippet.
Best practices for preventing mimikatz-based intrusions
Prevention measures should appear in any mimikatz-centric timeline snippet as actionable recommendations. These include system hardening, credential hygiene, and careful administrative practices.
Best practices:
- Enable LSA protection options and disable legacy credential storage features when possible.
- Enforce least privilege and limit local administrative accounts.
- Use multi-factor authentication and avoid reusing credentials across systems.
- Harden audit collection and forward logs to a centralized system for correlation.
Implementing these actions reduces the value of a mimikatz attack and shortens the useful window an attacker has to move laterally.
Red team considerations and ethical use in a mimikatz-centric timeline snippet
A balanced mimikatz-centric timeline snippet recognizes that mimikatz is used by both attackers and legitimate testers. When responsibly used, the tool helps organizations validate defenses under realistic conditions. In documentation and reporting, clearly mark tests and include artifact collection so defenders can refine detection logic based on controlled experiments.
Testing tips:
- Run simulations in isolated environments.
- Ensure notifications and stakeholders are informed before red team activities.
- Collect telemetry during tests to improve defender playbooks.
Building your own mimikatz-centric timeline snippet: template and tips
Use this template to create a compact timeline snippet for reporting or playbooks:
- Timestamp — Host — Event type — Evidence summary — Suggested action
Recommended workflow:
- Gather all relevant telemetry from endpoints and logs.
- Correlate events across systems and identify credential-related actions.
- Annotate the timeline snippet with artifacts and recommended containment steps.
- Share with response teams and update detection rules.
This structured approach yields a clear and actionable mimikatz-centric timeline snippet every time.
Conclusion: the value of a mimikatz-centric timeline snippet
A mimikatz-centric timeline snippet condenses complex forensic data into a readable, actionable chronology that helps defenders and analysts respond faster and learn from each incident. By tracing origins, mapping technical milestones, documenting real-world incidents, and listing mitigation and detection steps, your timeline snippet becomes a powerful tool for resilience. Use the templates and practices in this article to build timeline snippets that clarify how credential dumping unfolded in each case and to strengthen defenses against future misuse.
Frequently Asked Questions (FAQs)
1. What is a mimikatz-centric timeline snippet?
A mimikatz-centric timeline snippet is a focused chronological overview showing how the Mimikatz tool evolved, how it was used in cyber incidents, and how defenses developed in response. It helps security professionals visualize the key events and understand threat progression.
2. Why is a mimikatz-centric timeline snippet important for cybersecurity professionals?
It provides a structured way to analyze attacks, version changes, and mitigation efforts. By reviewing the timeline, analysts can quickly identify trends, common techniques, and effective defensive strategies.
3. How does a mimikatz-centric timeline snippet help in incident response?
During incident response, analysts can map out the sequence of credential dumping activities. The timeline helps pinpoint when Mimikatz was executed, what credentials were stolen, and how lateral movement occurred across systems.
4. What data sources are used to build a mimikatz-centric timeline snippet?
Typical data sources include Windows Event Logs, LSASS access alerts, Kerberos ticket anomalies, endpoint telemetry, and network logs showing authentication attempts and lateral movement.
5. Can Mimikatz still bypass modern defenses today?
While many modern systems include mitigations such as LSA protection and improved auditing, attackers often modify or recompile Mimikatz to evade detection. Ongoing vigilance, layered security, and monitoring are essential.